Would you know if your network was hacked? Untangle makes a hardware-based firewall that we recommend. All inbound and outbound internet traffic, hardwired and Wi-Fi, are monitored with activity alerts for suspicious connections.
It provides 24×7 protection for your internal internet-attached devices. In addition to the standard reports illustrated below, the router interface has extensive configuration options for the most demanding requirements. Online documentation and live support are some of the best we have seen.

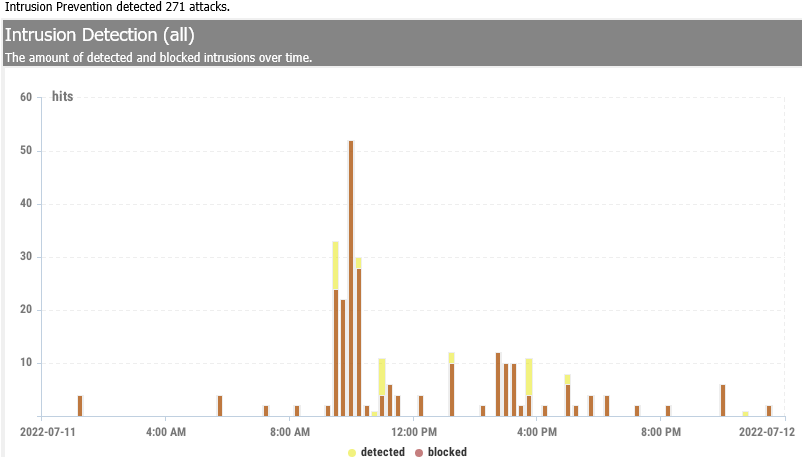
Blocked Intrusions
The Firewall application works to block traffic by IP addresses and ports. The port can be used to identify the protocol for well-behaved applications (such as legitimate web and email servers). Less than legitimate applications may use different ports or malicious users may deliberately use unwanted services on obscure ports.
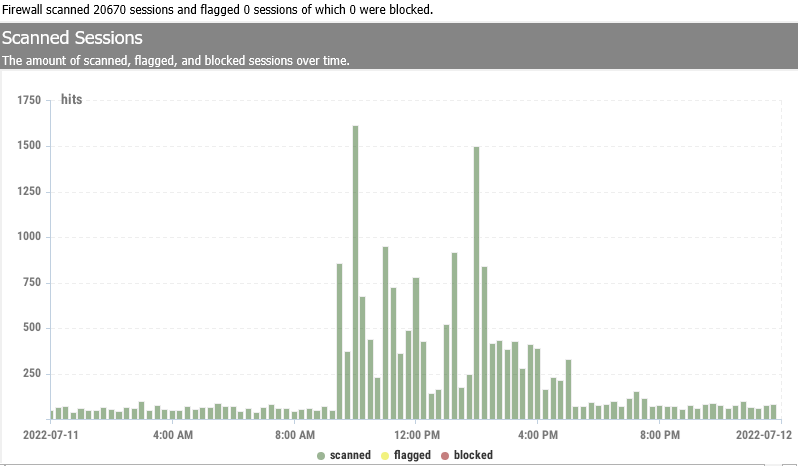
Scanned Sessions
The number of monitored and blocked sessions over time is recorded—the number of blocked sessions over time. The number of blocked sessions is grouped by username and clients. The number of blocked sessions is also grouped by server port.
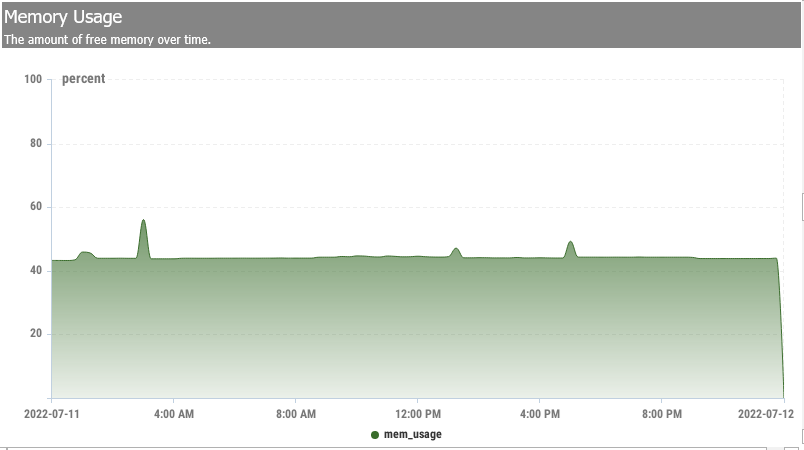
Memory Usage
The Memory Usage report displays the actual usage of the natural or physical RAM. This graph can give you an indication of an issue occurring over some time. Green indicates use, and white signifies free memory. The Swap Usage report, naturally, displays the amount of memory swap occurring on the appliance.
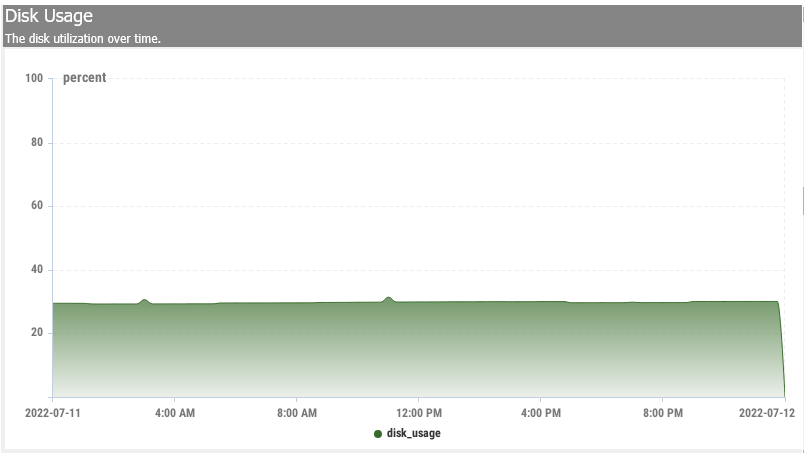
Disk Usage
What it is. This script will run and give you a detailed report on what is using your disk space. This script will not free up space, but only give you a signal.
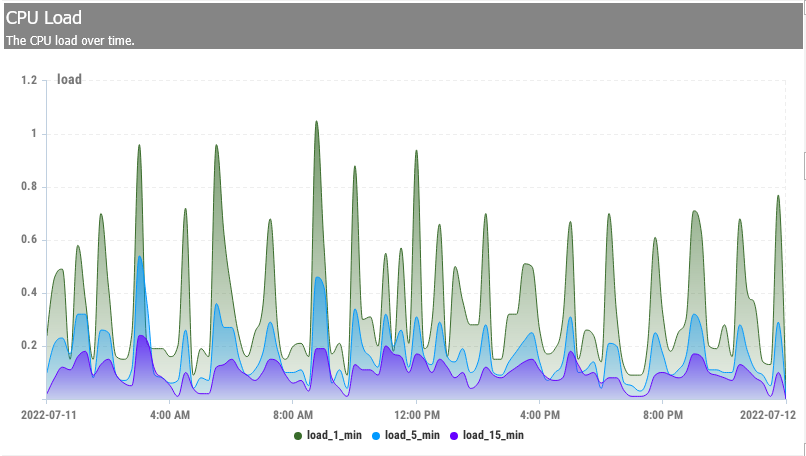
CPU Load
The average CPU load for any site will depend on the expected traffic load as seen by the CPU and can vary a LOT depending on the number of CPU cores and disk throughput of the server in question. Yes, the number of seats does matter. In a rough sense, a 1.0 CPU load corresponds to enough work to keep one CPU core busy full-time.
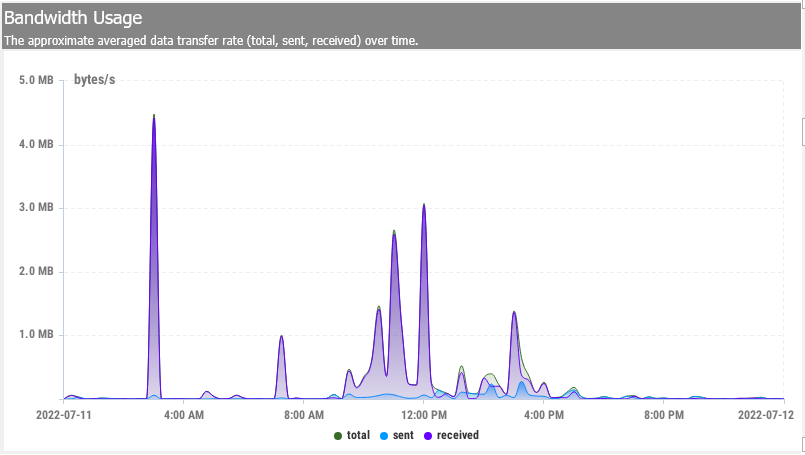
Bandwidth Usage
This allows you to monitor and control bandwidth usage on your network. It can be used to ensure that your network continues to operate smoothly and that bandwidth is shared optimally based on what is important to you. Many organizations struggle with bandwidth problems, such as students watching online videos or clients …
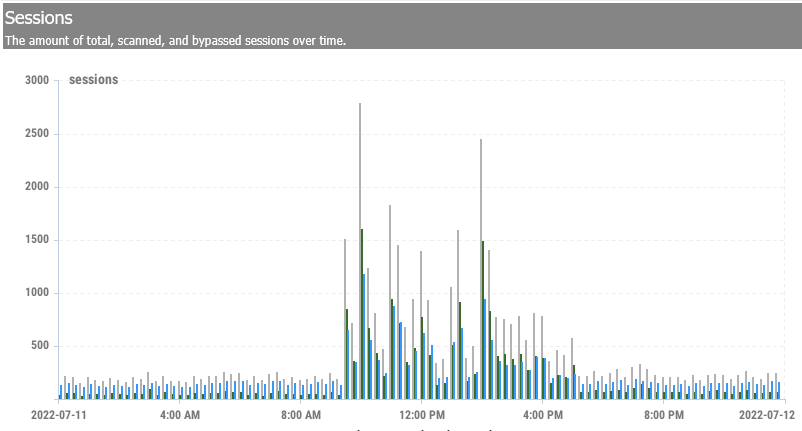
Sessions
Sessions provide a view of the current sessions (connections). Each row represents a single network session and its properties. As NG Firewall and all the apps learn more about a session, many will “attach” data to the session so it is globally visible and accessible to other apps.
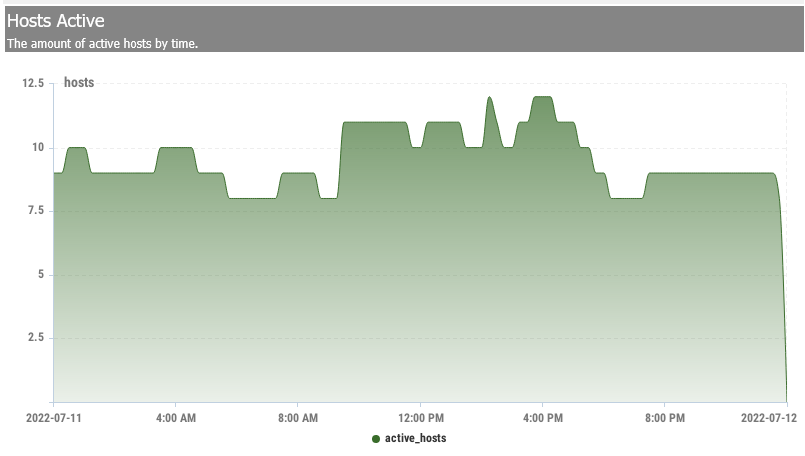
Hosts
Hosts view all current “hosts” or unique IP addresses on the local network (s). Each row represents a single host (IP address) seen on any LAN interface. As the NG Firewall scans and processes network traffic, the platform and many apps will save information about a host on the network.